As part of my presentation on “Drones and the everywhere war” at York, I decided to unpack this extraordinary claim made by John Nagl, one of the architects of the US military’s revised counterinsurgency doctrine:
We’re getting so good at various electronic means of identifying, tracking, locating members of the insurgency that we’re able to employ this extraordinary machine, an almost industrial-scale counterterrorism killing machine that has been able to pick out and take off the battlefield not just the top level al Qaeda-level insurgents, but also increasingly is being used to target mid-level insurgents.
It’s a remark I’ve discussed several times before. Nagl’s ‘killing machine’ is not limited to drone strikes, of course, but subsumes the ‘night raids’ and other Special Forces operations detailed in Jeremy Scahill‘s Dirty Wars. But at York I wanted to explore how those ‘electronic means of identifying, tracking and locating’ fed into drone strikes in Pakistan: and, thanks to Edward Snowden and Glenn Greenwald, I was able to get much closer to the belly of the beast.
I’d started the presentation with a riff on Josh Begley‘s attempt to persuade Apple to include his Drones+ app in the App store. Apple decided, for several contradictory and spurious reasons, to reject the app, and at his thesis defence Josh asked:
‘Do we really want to be as connected to our foreign policy as we are to our smart phones… Do we really want these things to be the site of how we experience remote war?’
Apple’s answer was ‘no’, clearly, but it turns out that others are intimately connected to drone strikes through their phones and e-mails, and it was this that I fastened on.
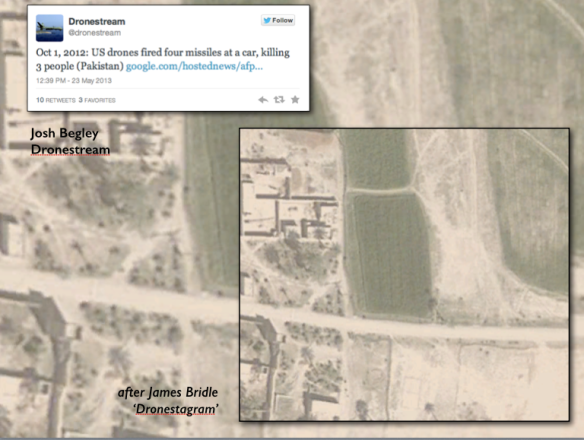
Josh, undeterred by Apple, went on to launch the Dronestream platform, from which he tweeted details of every known US drone strike. I combined one of Josh’s tweets for 1 October 2012 with a version of James Bridle‘s Dronestagram, which uses Instagram to post images of the location of drone strikes (I say ‘a version’ because Dronestagram was launched too late for this particular strike, so this is a mock-up; in any case, it’s difficult to pinpoint the locations from available reports with much precision, but the details for this strike are available via the Bureau of Investigative Journalism, as the second slide below shows):
We now know that this strike was made possible as a result of interceptions made by the National Security Agency’s Counter-Terrorism Mission-Aligned Cell (CT-MAC). Writing in the Washington Post on 16 October 2013 Greg Miller, Julie Tait and Barton Gellman explained how this strike had targeted Hassan Ghul:
Not quite ‘any doubt’; as they went on to note, ‘Although the attack was aimed at “an individual believed to be” the correct target, the outcome wasn’t certain until later, when “through SIGINT [signals intelligence] it was confirmed that Hassan Ghul was killed.”‘
So how did the intercept work? Not surprisingly, we don’t know for sure; but the map below of NSA’s ‘Boundless Informant‘ – another dimension of what I’ve been calling ‘the everywhere war’ – offers some clues. I’ve taken it from a report in the Guardian by Glenn Greenwald and Ewen MacAskill:
This is six months later, but it shows that Pakistan was, after Iran, the major focus of NSA’s surveillance and data mining operations (Miller and his colleagues had noted that “NSA threw the kitchen sink at FATA’, the Federally Administered Tribal Areas). It would be wrong to assume that the targeted killing of Ghul was the result of a simple hack into hotmail, and the Post report details the multiple methods used by NSA.
Still, the geography of covert surveillance shown on the map is revealing. Yesterday Greenwald returned to Boundless Informant and rebutted the charge that he had misinterpreted the meaning of this and other slides, and in doing so quoted from NSA’s own explanation of the system:
BOUNDLESSINFORMANT is a GAO [Global Access Operations, a branch of the NSA] prototype tool for a self-documenting SIGINT system. . . BOUNDLESSINFORMANT provides the ability to dynamically describe GAO’s collection capabilities (through metadata record counts) with no human intervention and graphically display the information in a map view, bar chart, or simple table. . . .
By extracting information from every DNI and DNR metadata record, the tool is able to create a near real-time snapshot of GAO’s collection capability at any given moment. The tool allows users to select a country on a map and view the metadata volume and select details about the collection against that country. The tool also allows users to view high level metrics by organization and then drill down to a more actionable level – down to the program and cover term.
It’s not too difficult to connect the dots and draw two more general conclusions. The first is that this is another, darker dimension to the ‘code/space’ and ‘everyware’ discussed in such impressive detail by Rob Kitchen and Martin Dodge:
My slide is just short-hand, of course, but you can see where I’m going, I hope – and, as we know from this week’s harrowing testimony on Capitol Hill about the murder of Mamana Bibi in Waziristan and Amnesty International’s report, Will I Be Next?, these operations and their algorithms work to turn ‘everyday life’ into everyday death. So I’ll be thinking more carefully about code/space and its implication in the individuation of later modern war, paying closer attention to the technical production of ‘individuals’ as artefacts and algorithms as well as the production of the space of the target: more to come.
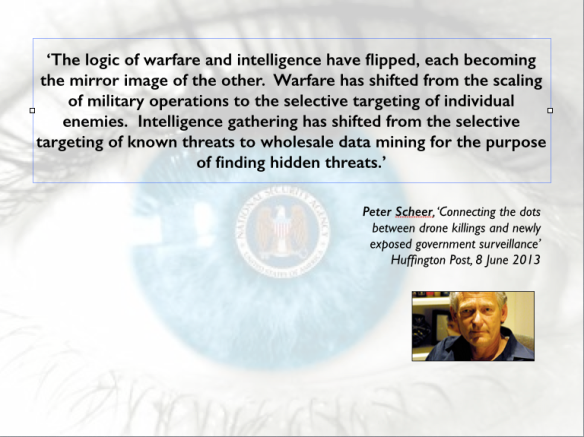
The second general conclusion I leave to Peter Scheer, who provides a more refined (and critical) gloss on John Nagl’s comment with which I began:
I’m incorporating these and other developments into the revised and extended version of “Moving targets and violent geographies” which will appear in The everywhere war, but I hope this bare-bones account (and that first draft, available under the DOWNLOADS tab) shows that my posts are more connected than they must sometimes appear… The slides were pulled together on the day I gave the presentation, so forgive any rough edges.






Pingback: Drones and the Distributed Geography of “Homeland” | Musings on Maps
Pingback: Dirty Dancing online | geographical imaginations
Pingback: Killing the SIMs | geographical imaginations
Pingback: Meta-dating | geographical imaginations
Reblogged this on Oren Stark and commented:
Reading about code/space while also reading The Global Genome by Eugene Thacker makes me consider the question: is space the container or the material ‘itself’? Space and (bio)matter as encoded, either always already as an information system or transformable/translatable from matter to information, requires a presumption of the “knowability” of that information, i.e. what the data means. Unwittingly, I am positing that information:data as phenomena:noumena, where the NSA believes that when it (or an algorithm) ‘looks’ at data, it can determine knowable information, producing knowledge that validates itself merely by the processes of its production. Just a thought.